Trusted Locations for 2FA
When you successfully log in from a device, your location is added to your list of trusted locations. When you log in from a trusted location, you can use your username and password without a verification code, as Paligo knows you have verified that location before.
Your "trusted locations" are listed in your user profile. You can view them there, and if necessary, you can remove them too. For example, if you think a login looks suspicious because it is from a location you do not recognize, you can delete the location.
To see the "trusted locations" that are associated with your user account:
-
Select the avatar in the top right corner.

-
Select My Profile.

-
Select the Trusted Devices tab.
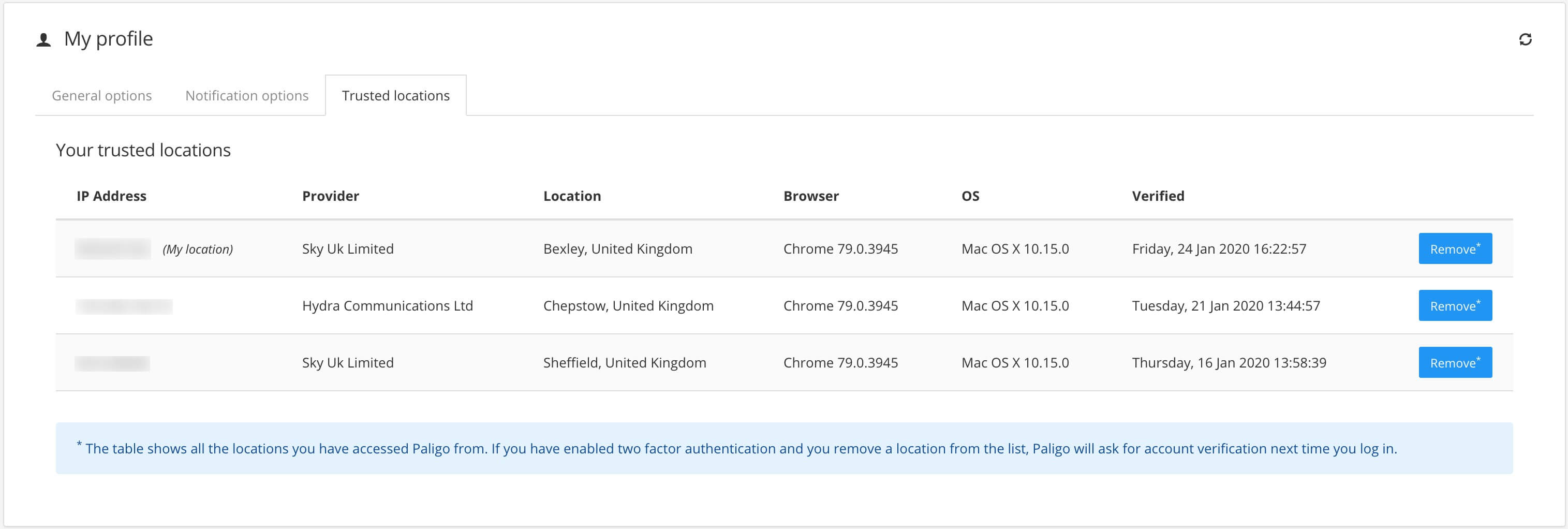
The Trusted Devices tab contains a list of the "trusted devices" that are associated with your user account. For each device, Paligo keeps a record of the IP address, Internet Service Provider (ISP), approximate Location, Browser and version, operating system (OS) and version, and the time and date that you Verified the device.
-
If you see a location that looks suspicious, you can delete it by selecting the Remove button for that location. If you remove a location it is no longer trusted, so any login attempt from that location will need to be verified.